System Overview
Components
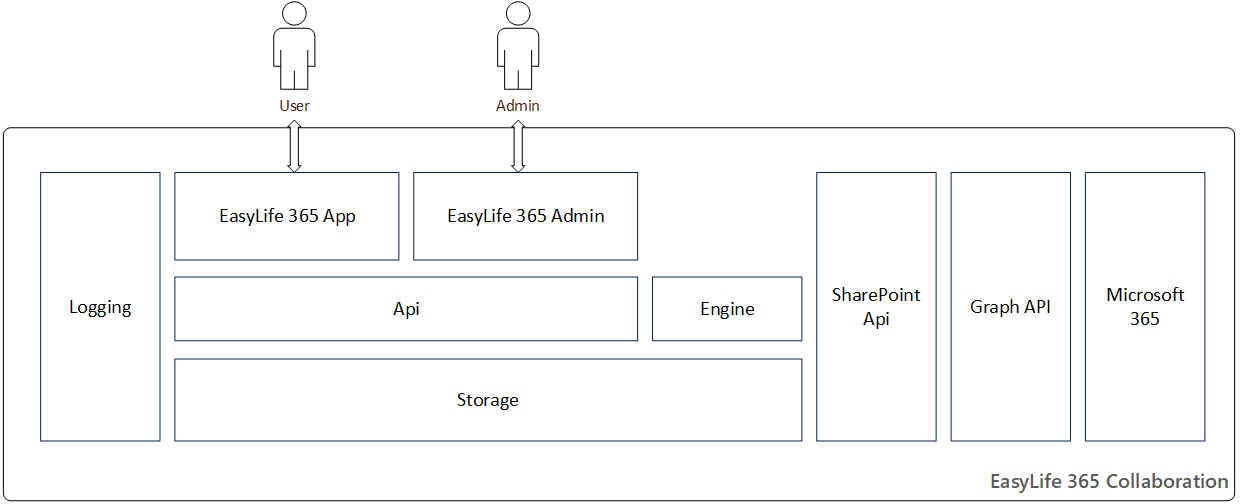
EasyLife 365 Collaboration consists of several components hosted on Azure, providing the necessary provisioning logic and capabilities for all users.
App
The EasyLife 365 Collaboration App is a web application accessible through a web browser and directly through Teams. It uses a dedicated Entra ID application on the Microsoft Identity platform for authentication, ensuring security with Microsoft standards. The app provides an overview of the resources owned by a user, including all necessary compliance requirements. Users can also request new resources specified by those allowed to configure EasyLife 365 Collaboration through the EasyLife 365 Admin.
Admin
The EasyLife 365 Admin is a web application hosting the configuration pages for EasyLife 365 Collaboration. It is accessible through a web browser and can be restricted to selected users within your organization. Typically, permissions for this app are assigned to a small subset of administrators via a security group. Authentication is managed by an Entra ID application on the Microsoft Identity Platform, allowing you to limit access and enforce additional authentication techniques using conditional access policies.
API
The EasyLife 365 API is accessed by the EasyLife 365 Collaboration App and the EasyLife 365 Admin to manage the necessary information stored in the back-end storage. This web app is secured through a dedicated Entra ID app using the Microsoft Identity Platform. The EasyLife 365 API uses Microsoft Graph to interact with the Microsoft 365 environment, with access to endpoints secured using custom security scopes associated with your EasyLife 365 Collaboration App and users.
Engine
The EasyLife 365 Collaboration Engine is an Azure Function responsible for provisioning new resources and performing regular compliance checks in your tenant. It also sends notifications to users and administrators via a SendGrid account and can send notifications through Teams or other applications using the Webhook feature.
Storage
The EasyLife 365 Collaboration configuration (e.g., templates, policies, unique keys) is stored in Azure Table Storage. The storage account is accessible by the EasyLife 365 API and the EasyLife 365 Collaboration Engine.
Logging
Application Insights is used to log operations performed by EasyLife, maintaining 90 days of logs containing metadata of processed groups and emails of users receiving notifications.
Microsoft Graph
Microsoft Graph is used by EasyLife 365 components to interact with the Microsoft 365 tenant. It provides a unified programmability model to access data and intelligence in Microsoft 365, Windows 10, and Enterprise Mobility + Security.
Entra ID
The Microsoft Identity Platform is used in combination with Entra ID to secure access to all EasyLife 365 components. The EasyLife 365 Collaboration App, EasyLife 365 Admin, and EasyLife 365 API have dedicated Entra ID app registrations that can be secured using techniques such as Conditional Access.
Architecture and Data Flow
This section provides an overview of how EasyLife 365 components interact and how the environment is accessed.
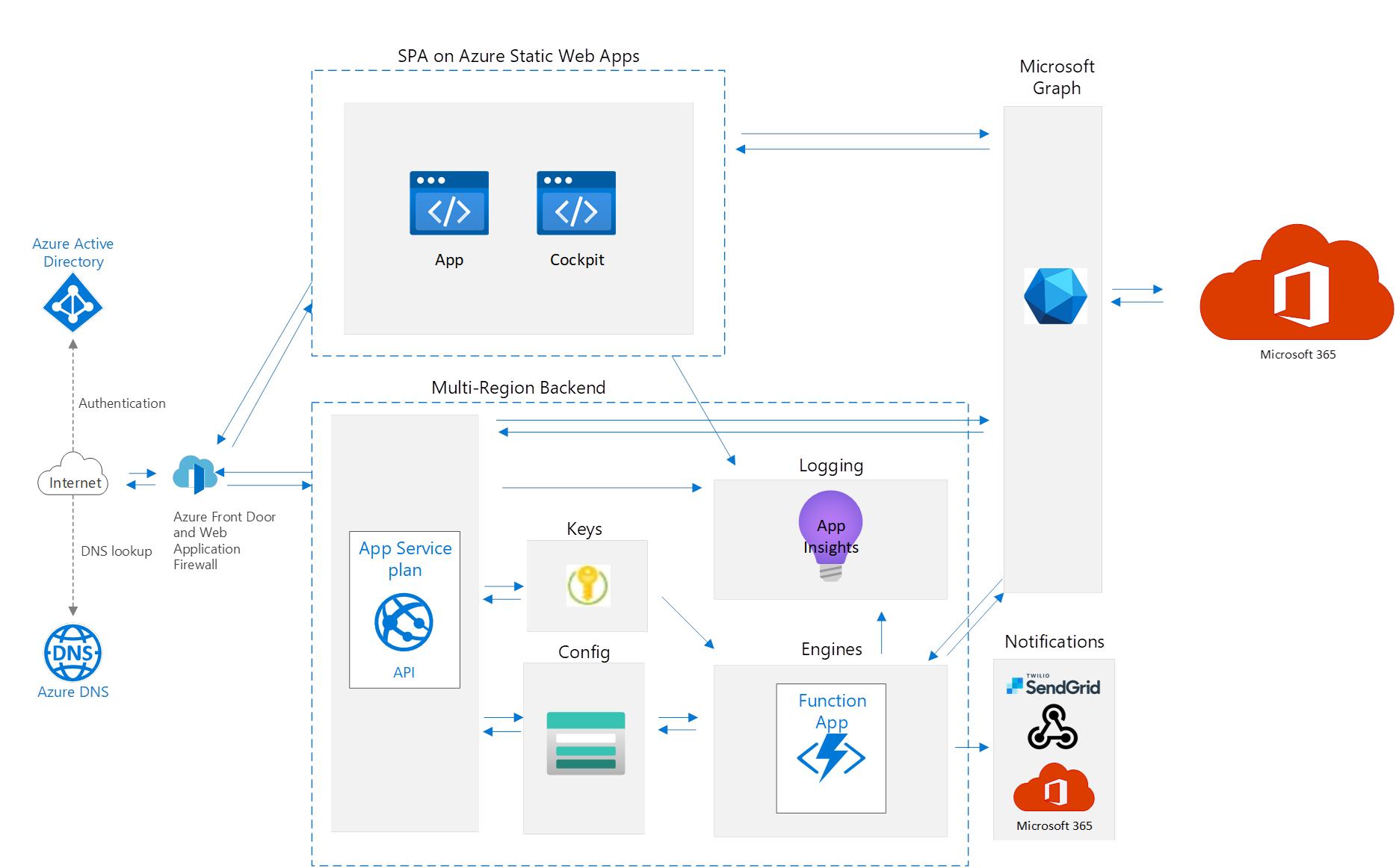
All components are secured behind an Azure Virtual Network, with all external internet traffic to the EasyLife 365 Collaboration environment routed through an Azure Front Door and Web Application Firewall for load balancing and security. Only a few services, such as our GitHub for automated deployment and selected engineers over a secured network for emergency purposes, have access to the environment.
Incoming user traffic is routed through an Azure Front Door and Web Application Firewall, which secures the web applications and the environment from documented vulnerabilities. See details here. All endpoints are secured using Entra ID applications with the Microsoft Identity Platform. Interactions between internal applications are secured with role-based access control and managed identities. Azure Key Vaults, accessible only by managed identities and selected security engineers at EasyLife, store security keys when managed identities cannot be used.
The EasyLife 365 Collaboration App and EasyLife 365 Admin use Microsoft Graph with delegated identity permissions to perform activities on your Microsoft 365 tenant. This means users can only perform operations they are authorized to execute in your Microsoft 365 tenant.
Users can request new resources in the EasyLife 365 Collaboration App based on template configurations from the EasyLife 365 Admin. All CRUD operations on these configurations are processed through the EasyLife 365 API. The EasyLife 365 Collaboration App reads the configuration information, while the EasyLife 365 Admin allows you to create, update, and delete settings as needed.
The EasyLife 365 Collaboration Engine handles new resource requests from users, creating new resources with Microsoft Graph. All operations are executed in the context of the EasyLife 365 Collaboration App.
EasyLife 365 stores information in multiple storage locations and accounts to ensure resiliency and performance. Data partitioning is managed using the customer's TenantID, ensuring correct access to resources with security tokens from the Microsoft Identity Platform.
Endpoints
EasyLife 365 Collaboration Applications communicate with the following endpoints. Ensure your firewalls and content filters allow access to these URLs. EasyLife 365 communicates exclusively over https (TCP/443).
| Endpoint | Protocol | Comment |
|---|---|---|
| https://onboarding.easylife365.cloud | https | The EasyLife 365 Onboarding |
| https://app.easylife365.cloud | https | The EasyLife 365 Collaboration App |
| https://admin.easylife365.cloud/collab | https | The EasyLife Admin portal |
| https://api.easylife365.cloud | https | The EasyLife API |
| https://cdn.easylife365.cloud | https | Content delivery |
| login.microsoftonline.com | https | Entra ID Authentication |
| graph.microsoft.com | https | Microsoft Graph API |
| dc.services.visualstudio.com | https | Anonymous telemetry data |
Required Permissions
EasyLife 365 Collaboration uses the Microsoft Identity Platform to manage authentication and authorization against your Microsoft 365 tenant. It uses Microsoft Graph and the SharePoint REST API to access your resources. EasyLife 365 Collaboration employs the EasyLife 365 Admin and EasyLife 365 Entra ID application to perform operations in the context of a user or administrator.
EasyLife 365 Collaboration is a certified Microsoft 365 application, meaning it has undergone a thorough security audit. The app meets security controls derived from leading industry standard frameworks such as SOC 2, PCI DSS, and ISO 27001. Certified apps demonstrate strong security and compliance practices to protect customer data. Details about the required permissions can be found on the Microsoft 365 App Certification website.
Data Location & Retention
EasyLife 365 Collaboration prioritizes the protection of customer information by minimizing data stored in our environment. Workflow data is directly saved in the customer's Entra ID environment and linked to the lifetime of Entra ID resources such as Microsoft Teams and Entra ID Guest Accounts.
All activities performed by the EasyLife 365 Entra ID application, such as resource creation and changes based on policy settings, are monitored in Microsoft Audit Logs and associated with the Entra ID Application EasyLife 365. Activities performed in the administrative console are recorded in audit logs with the Entra ID application EasyLife 365 Admin. The retention period for these logs can be configured in the customer's tenant.
Configuration data, including templates, policies, approval states, and notification settings, are stored in a dedicated Azure Subscription in our European data center. Customers from the Americas and Asia Pacific can request their configuration data to be saved in their respective regions. This data is retained as long as the customer has a valid EasyLife 365 license and is automatically erased 90 days after the license expires. Configuration and approvals backups are deleted after 180 days.
For internal support and troubleshooting, EasyLife keeps track of operations performed by the EasyLife 365 Collaboration App and EasyLife 365 Admin Entra ID app for 90 days. During this period, information such as Microsoft 365 Group Metadata (e.g., Title, Description) and user contact data (e.g., email address, preferred language) is saved. Sign-in logs to EasyLife are tracked for 90 days.
Mail notification history is monitored for 7 days if the SendGrid notification option is selected. This rule does not apply to Microsoft Shared Mailboxes. User tickets are tracked for 6 months until closure.